Pentest Target
Define where our pentesters can find your asset.
Define what you want our pentesters to test.

Once you’ve reviewed your asset, you can define pentest requirements.
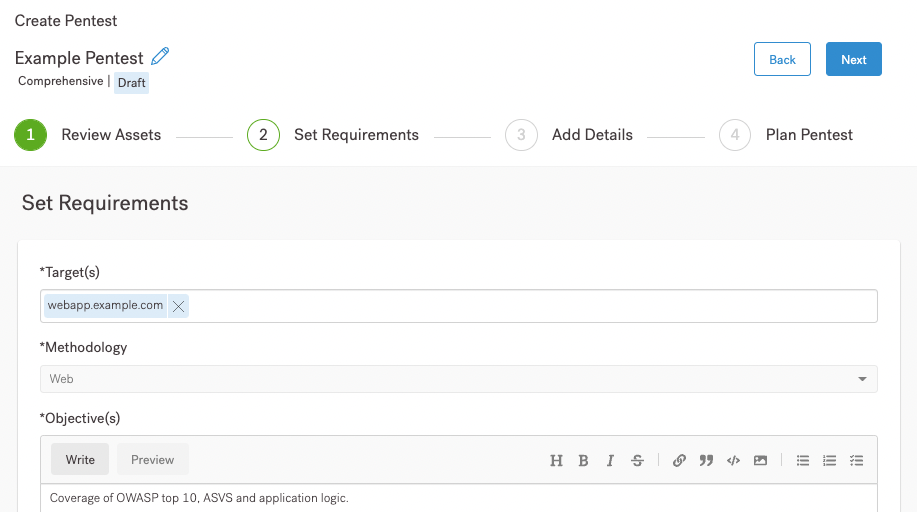
On this page of the UI, you can:
If you’re not sure what to include in the UI, follow the links associated with each bullet. If you’re experienced with defining pentests, fill out the page, and continue to Pentest Detail Requirements.
We use the penetration testing methodologies listed on the page. If you want to know more about each methodology, navigate to the page associated with your asset.
If you start at the top of the pentest requirements page, your next step is to specify a target.
Define where our pentesters can find your asset.
Your pentesters need dedicated accounts to test your systems.
Every asset is unique. What do your pentesters need to know about it?
Your pentesters need to know the technologies behind your asset.