Cloud Configuration Pentests
Our pentesters test your assets rigorously.
We support penetration testing of systems in the following cloud environments:
- Amazon AWS
- Google Cloud Platform (GCP)
- Microsoft Azure
While we perform many of the same tests on different cloud configurations, each environment has unique testing requirements.
Cloud Network Pentest
We test cloud assets based on the cloud pentest methodologies listed on this page. If you want a network pentest of your cloud asset, ask us for an External Network Pentest.
Common Requirements
Cobalt assesses your selected cloud environment, as well as all internal and external components. Cobalt follows an industry standard methodology primarily based on:
- Best practices established by your cloud provider
- OWASP standards for Cloud Providers (PDF) and Application Security Verification Standard (ASVS).
The Cobalt team of pentesters do not need access to the underlying web application source code, unless you specify it as a requirement.
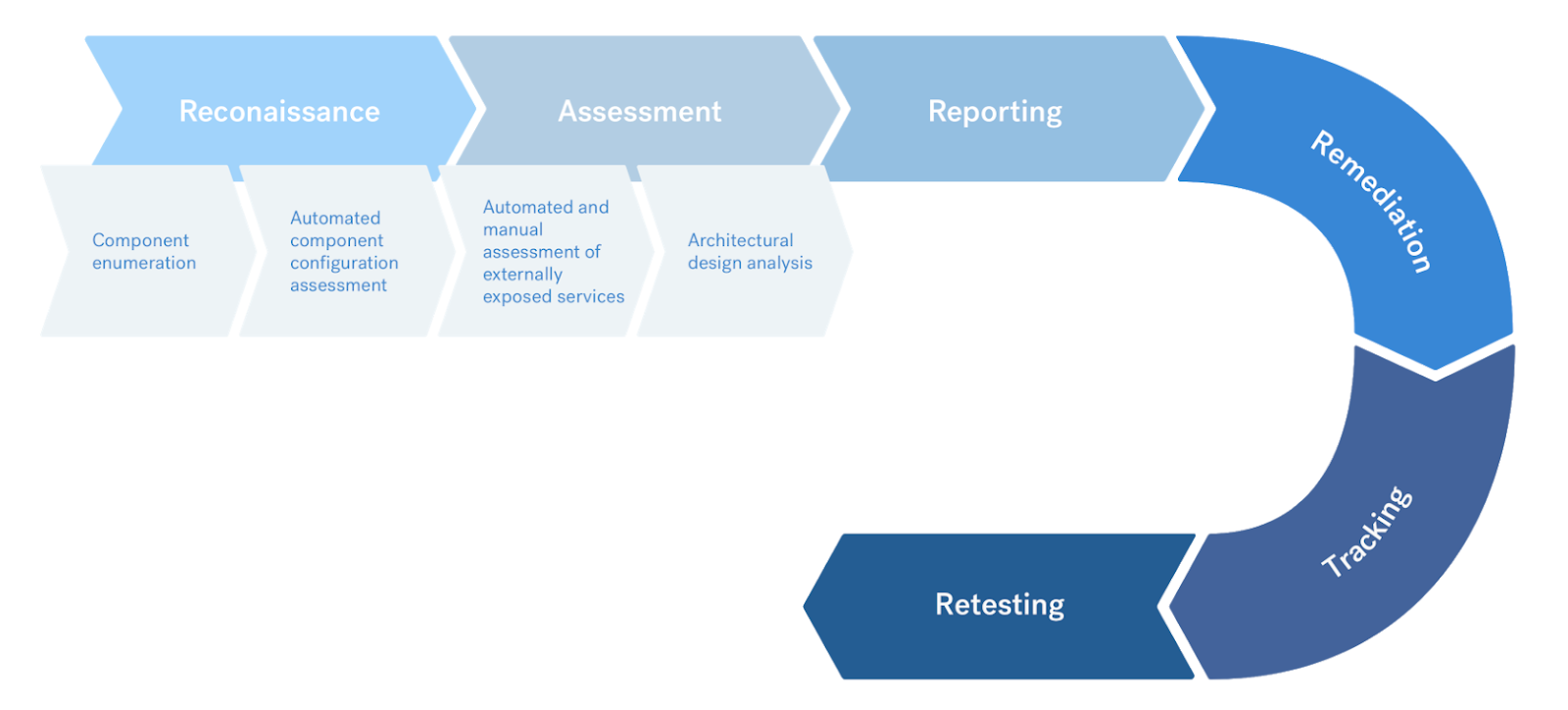
We follow an industry standard methodology primarily based on the OWASP ASVS Testing Guide. Our team takes the following steps to ensure full coverage:
- Target scope reconnaissance
- Component enumeration
- Based on automated component discovery
- Automated component configuration assessment
- Detail risks, based on Center for Internet Security (CIS) best practices
- Automated / manual review of externally exposed services
- Basic vulnerability assessments
- Architectural design analysis
- Reporting, triaging, and retesting
In general, the cloud providers that we work with no longer need to know before we perform our pentests. However, each cloud provider may have their own procedure. We’ve included links to procedures that we know of in the section for each provider.
Source IP Addresses
Cloud providers may need to include IP addresses associated with pentest traffic in their allowlist. We’ll share these addresses when you create an actual pentest.
Testing Parameters
When you create a pentest that involves a cloud provider, we’ll share the information that your cloud provider may require, including:
- Peak bandwidth
- Peak queries per second
- Escalation traffic requirements
- Emergency contact information
Amazon AWS
Our pentesters need access to test your AWS systems. To that end, you should prepare:
- A dedicated AWS account for each pentester, with access to each target system.
- Identity and Access Management (IAM) API credentials for each affected AWS account.
- Include the following managed policies for the pentest user or role:
SecurityAuditViewOnlyAccess
- Include the following managed policies for the pentest user or role:
- Identity and Access Management (IAM) API credentials for each affected AWS account.
These are the required policy Amazon Resource Names (ARN):
arn:aws:iam::aws:policy/SecurityAudit
arn:aws:iam::aws:policy/job-function/ViewOnlyAccess
You should also include the architecture of your cloud configuration.
What is covered
Cloud Configuration Reviews meet the Security standards based on the Center for Internet Security (CIS) Benchmarks. AWS CIS Benchmarks cover IAM, Storage, Logging, Monitoring, and Networking.
Specific checks categories that are covered as part of the Pentest
- AWS Cloudtrail
- AWS Cloudwatch
- AWS EC2
- AWS ELB
- AWS IAM
- AWS RDS
- AWS Redshift
- AWS Route 53
- AWS S3
- AWS SES
- AWS SNS
- AWS SQS
- AWS VPC
Google Cloud Platform (GCP)
Our pentesters need access to test your GCP systems. To that end, you should prepare:
- A dedicated GCP account for each pentester, with access to each target system.
- GCP access keys.
- Identity and Access Management (IAM) API credentials for each affected GCP account.
- To provide API credentials, use a (service) account with Viewer and Security Reviewer permissions.
What is covered
Cloud Configuration Reviews meet the Security standards based on the Center for Internet Security (CIS) Benchmarks. GCP CIS Benchmarks cover IAM, Storage, Logging, Monitoring, Virtual Machines, Cloud SQL DB Services, BigQuery, and Networking.
Specific checks categories that are covered as part of the Pentest
- GCP Identity and Access Management
- GCP Logging and Monitoring
- GCP Networking
- GCP Virtual Machines
- GCP Storage
- GCP Cloud SQL Database Services
- GCP BigQuery
Microsoft Azure
Our pentesters need access to test your Azure systems. To that end, you should prepare:
- A dedicated Azure account for each pentester, with access to each target system.
- Identity and Access Management (IAM) API credentials (read-only) for each dedicated account.
What is covered
Cloud Configuration Reviews meet the Security standards based on the Center for Internet Security (CIS) Benchmarks. Azure CIS Benchmarks cover IAM, Microsoft Defender, Storage Accounts, Database Services, Logging, Monitoring, Key Vault, AppService and Networking.
Specific checks categories that are covered as part of the Pentest
- Identity and Access Management
- Microsoft Defender
- Storage Accounts
- Database Services
- Logging and Monitoring
- Networking
- Virtual Machines
- Key Vault
- AppService
Other Cloud Providers
We’ve done pentests on other cloud providers. You can refer to the Common Requirements listed earlier.
Note
Cloud providers may require notification before we perform a pentest. For more information, consult the documentation for your cloud provider.Additional Requirements
You’re welcome to define additional test objectives. If you follow best practices other than OWASP, ASVS, or OSSTMM, let us know. Include a link or other documentation. If it’s a “well-known” security practice, our pentesters probably already know them!
If you have special instructions for a pentest, add them later, under Special Instructions.