Pentest States
Describes the status of your pentest.
Explore the stages of the Cobalt Pentest as a Service (PtaaS) program.
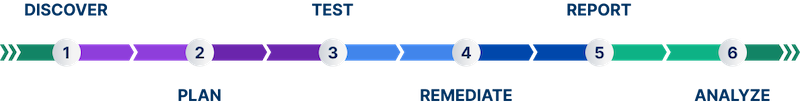
| Stage | Description | |
|---|---|---|
| 1 | Discover | Prepare for the pentest engagement.
|
| 2 | Plan | Plan, scope, and schedule your pentest.
|
| 3 | Test | Pentesters test your asset using various pentest methodologies and techniques.
|
| 4 | Remediate | The testing process is complete. Remediate findings that pentesters discovered.
|
| 5 | Report | Download the pentest report to view a summary of vulnerabilities in your software. Share the report with stakeholders.
|
| 6 | Analyze | Once the pentest is complete, analyze the security posture of your asset.
|
Describes the status of your pentest.
Learn what the Cobalt coverage checklist is and how to use it.