Coverage Checklist
Learn what the Cobalt coverage checklist is and how to use it.
The Cobalt coverage checklist is a list of checks that pentesters use throughout a pentest to ensure that a baseline of security controls are in place. The list is based on security standards such as OWASP Application Security Verification Standard (ASVS).
The coverage checklist differs for each asset type.
- For Web, API, and Mobile assets, the list is based on the OWASP ASVS Level 3.
- For other pentest methodologies that are not covered by OWASP, we defined a custom baseline based on the input from domain experts.
How Pentesters Work with the Coverage Checklist
The coverage checklist is not intended to describe how to perform a pentest. Its purpose is to help coordinate the work of pentesters and to ensure the baseline coverage. Usually, the work of pentesters goes well beyond the coverage checklist.
Pentesters use the coverage checklist collaboratively throughout a pentest.
- Once a pentester has completed a specific check, they mark this item as tested.
- Other pentesters see which items have been tested and which they need to work on.
- Multiple pentesters can cover the same security controls.
How to Use the Coverage Checklist
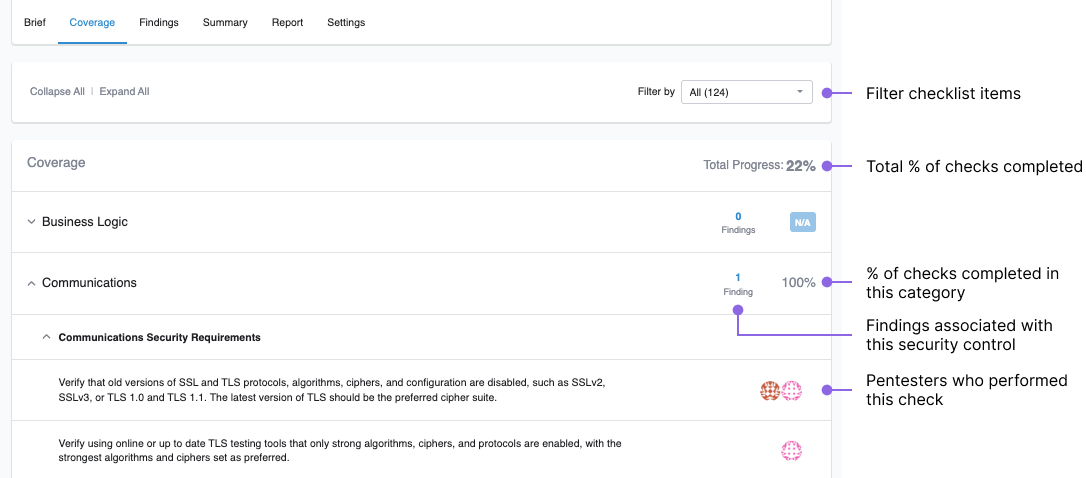
On the pentest page, navigate to the Coverage tab. The coverage checklist is available once the pentest moves to Planned.
- Track the testing progress in real time, for each security category or for the entire pentest.
- Identify categories that have associated findings. Work on these security controls to minimize risks.
- Analyze which security controls have passed the test. If pentesters found vulnerabilities in these categories earlier, it means that you’ve successfully remediated the issues.
Last modified May.05.2023