Complete an In-House Pentest (For Pentesters)
This page is for In-House Pentesters who complete In-House Pentests. If you’re a pentest manager, please read how to run an In-House Pentest.
Getting Started
As an In-House Pentester, you can perform pentests for your organization on the Cobalt platform. Once you’ve received an email invite to work on a pentest, follow the link in the email to get started.
When you sign in to Cobalt as an In-House Pentester, you land on the Pentests page showing pentests to which you’re assigned. Navigate to the pentest you plan to work on.
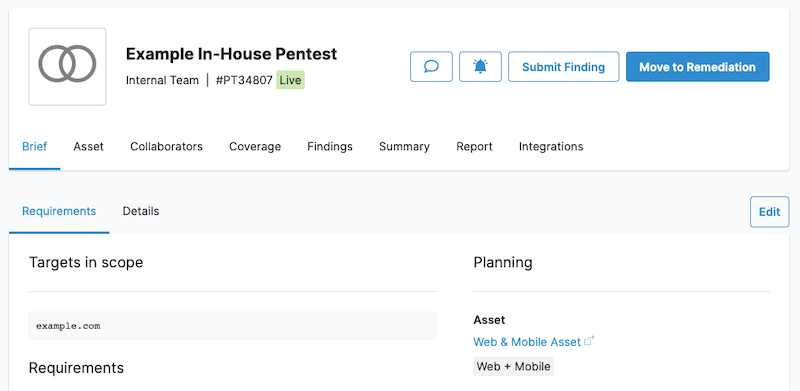
From the pentest page, you can:
- Review the pentest scope and asset details.
- Submit findings that you discover.
- Collaborate with your organization members in the chat.
- Update the coverage checklist as you progress through the pentest.
- Use the Vulnerability Detector tool to automatically identify potential vulnerabilities.
- Write a pentest report.
Read Pentest Requirements
Before you start testing the asset, carefully read pentest requirements. If you have questions, get in touch with your organization.
From the Brief tab on the pentest page, navigate to Requirements and Details. Here, you can see the following:
- Pentest timelines, under Test Period
- Pentest targets
- Test requirements
- Credentials to access the system
- System description
- Other details needed for the pentest
To learn more about the asset you’re testing, navigate to the Asset tab. Read about the asset types we support on the Cobalt platform.
Test the Asset
Start testing the asset. Use techniques and tools appropriate for the asset type you’re testing. Collaborate with your team to update them on your progress.
Collaborate on the Pentest
Communicate with pentesters and Pentest Team Members in the chat throughout a pentest. To open the chat, select the chat icon ![]() on the pentest page.
on the pentest page.
Use the chat to:
- Inform your team about the vulnerabilities that you discover.
- Ask questions about the pentest scope and asset.
- Submit any additional comments.
To view who collaborates on the pentest, including pentesters, go to the Collaborators tab.
Follow Pentest Methodologies
A pentest methodology outlines the process a pentester follows to discover vulnerabilities.
You can apply pentest methodologies that Cobalt pentesters use. These methodologies are based on the industry best practices.
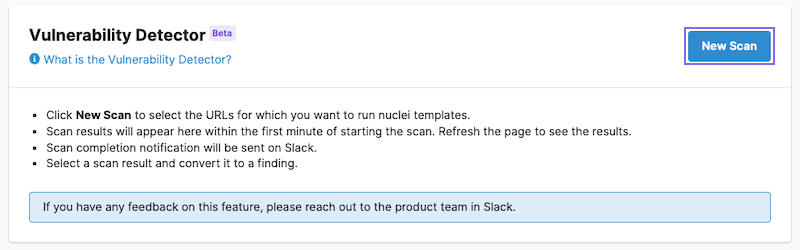
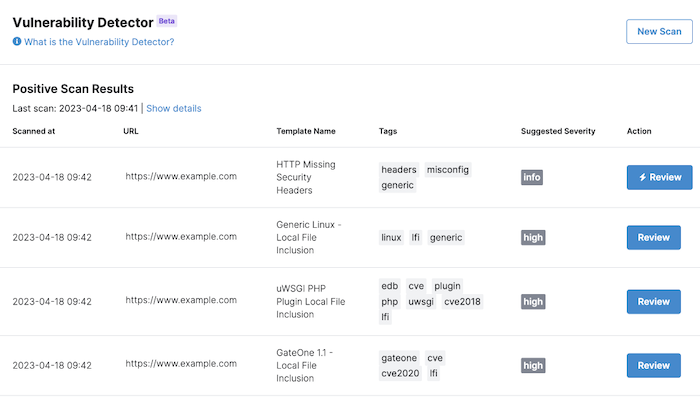
Use the Vulnerability Detector
To save time throughout a pentest, use testing tools available on the Cobalt platform.
The Vulnerability Detector is a vulnerability scanner tool powered by Nuclei. It scans assets for potential vulnerabilities using Nuclei templates.
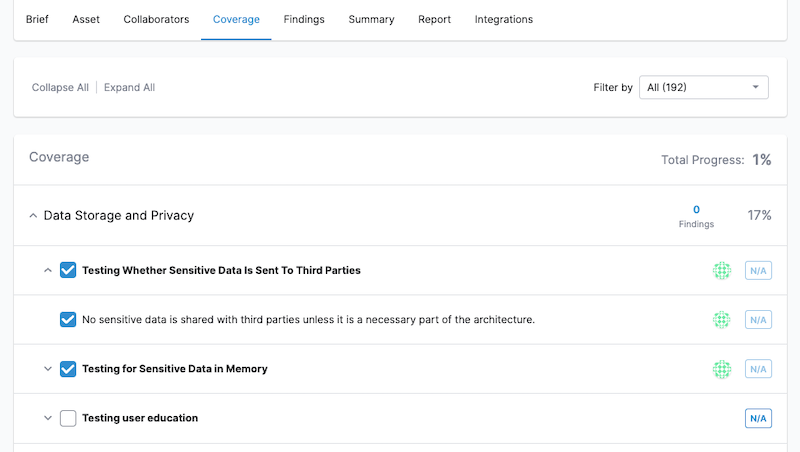
Update the Coverage Checklist
The Cobalt coverage checklist is a list of checks that pentesters use throughout a pentest to ensure that a baseline of security controls are in place. The list is based on security standards such as OWASP Application Security Verification Standard (ASVS).
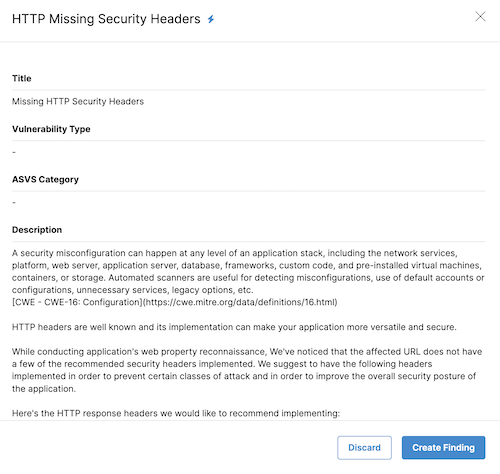
Submit Findings
A finding is a vulnerability that a pentester reports during a pentest. A finding report includes evidence of the issue, an explanation of the problem and solution, and a context as to how this may impact the organization’s systems.
The vulnerability taxonomy that Cobalt provides helps you increase the quality of your finding reports and streamline the documentation process. We’ve categorized the most common vulnerability types, added boilerplate descriptions, and listed remediation tips for specific categories.
Note
You can submit findings when the pentest is Live. When the pentest moves to Remediation, you can no longer submit findings.To report a vulnerability that you discovered:
- On the pentest page, select Submit Finding.
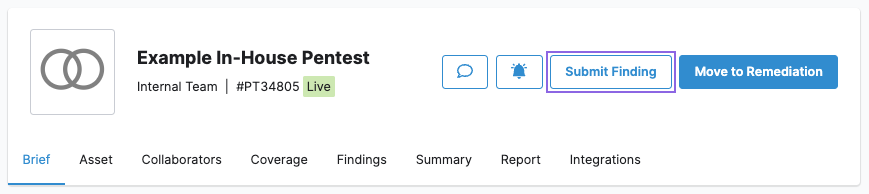
- Describe the finding. Make sure to provide thorough information about the vulnerability to help your organization fix it. If needed, add attachments such as screenshots, HTML files, or scripts.
- Title: The title should be concise and contain an overview of the issue, such as Stored Cross Site Scripting or IDOR in /api/users/{id}.
- Type: Select the vulnerability type from the list.
- We’ve categorized and listed the most common types. Start typing in the input field, and select one of the predefined options.
- Select the ASVS category.
- Description: A high-level summary of the identified issue and an explanation of the impact it could cause if exploited successfully. Focus on how the issue works in general, and then add specific details to other fields.
- Review and edit the description that populates in the field. We provide boilerplate descriptions to help you speed up the documentation process.
- Affected URLs: Add affected URLs showing where the vulnerability exists. Don’t include long URL strings here, add them to the HTTP Request field instead.
- Proof of Concept: Write steps to reproduce the issue. Ensure that users with appropriate technical skills can reproduce the issue following your instruction.
- Severity: Describe the overall impact of the vulnerability could be if exploited successfully. Keep the impact description as realistic as possible, instead of writing what may theoretically happen. The best way to do this is to stick to one immediate consequence, such as “an attacker could gain access to a user account,” and not speculate what the attacker could do with that access (as they could do something unexpected).
- Suggested Fix: List remediation tips based on the industry best practices. We provide boilerplate tips for some vulnerability types. You can include links to resources such as OWASP cheat sheets.
- Prerequisites: The attacker’s authentication credentials required before exploiting the vulnerability. For example, “an attacker must have admin credentials”, “attacker must be a person in the middle-man position,” or “N/A” if the application issue requires no authentication.
- HTTP Request: Provide a full request from your proxy to show how an endpoint was exploited. For each request, add a note about the instance it relates to.
- You can attach files or add comments to the finding under Activity. Use this section to discuss the finding with your organization.
- When you’re done, you can:
- Save the finding as a draft and go back to it later.
- Submit the finding by selecting Submit for Triaging.
Triage Findings
- Triage the finding to verify that it’s a valid issue. If possible, collaborate with your pentest team on triaging.
- Based on the results of triaging, select a status from the State list:
- Declined: The vulnerability is not valid.
- Duplicate: The vulnerability already exists on this pentest.
- Out of Scope: The vulnerability is valid, but it’s out of scope for this pentest.
- Pending Fix: The vulnerability is a valid issue.
- Assign the likelihood and business impact to the finding. The severity level is calculated based on these parameters.
- Select Submit evaluation to confirm.
Your organization members get notified and can remediate the finding.
Note
To change the severity level of a finding, move the finding back to Triaging.Move the Pentest to Remediation
Once the testing process is complete, you can move the pentest to Remediation. Select Move to Remediation on the pentest page.
- Before moving the pentest to Remediation, finalize and validate all findings in the Draft and Triaging states.
- Your organization can move the pentest to Remediation before you do so.
- When you mark the pentest report as Final, the pentest moves to Remediation.
- You can’t move the pentest back to the Live state.
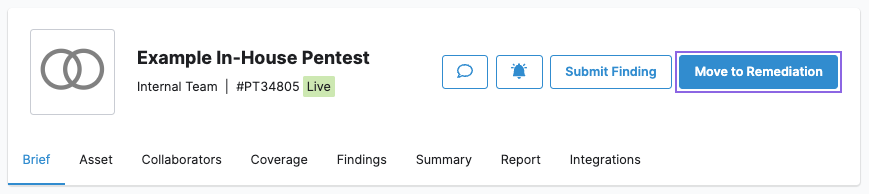
Retest Findings
Once your organization members have fixed a finding, they submit it for retest. You get an email alert and see a notification in the Cobalt app.
- On the pentest page, navigate to Findings, and select Retest to filter findings that are ready for retest.
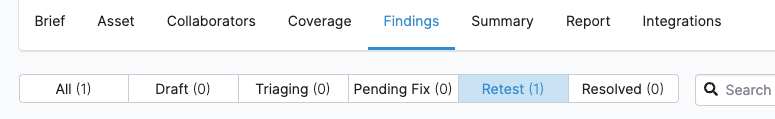
- Retest the finding to make sure that the issue was fixed.
- If you need to upload files or add comments, use the Activity section.
- When finished, change the finding state to:
- Fixed, if you can’t reproduce the issue.
- Pending Fix, if the issue persists. You can leave a comment on the finding to provide more details.
Write a Pentest Report
To summarize the pentest, write a report. A pentest report is a high-level summary of the pentest engagement.
For specific guidelines (if any), get in touch with your organization. Make sure you clarify your organization’s expectations for In-House Pentest reporting.
Learn more about the report types and report sections.
Note
The report content is fully flexible for In-House Pentests.
- On the pentest page, navigate to the Report tab, and select Edit Report.
- (Optional) To use boilerplate content describing vulnerabilities, select Auto-generate Content. This will override your existing content, so make sure to save it outside the platform before confirming your action.
- If you’re not familiar with the Markdown syntax elements, you can learn more about Markdown on external resources, such as in this Markdown Cheat Sheet.
- Complete each section of the report. Some fields already contain boilerplate information. Here are the guidelines that Cobalt pentesters follow, for your reference.
- Executive Summary: Sets the parameters for the pentest. The dates, methodologies used, number of pentesters, and asset scoped for the test. This section makes up the Attestation Letter, and appears in all other formats.
- Executive Analysis: High-level overview of the most significant findings or overall narrative of the pentest. This usually includes a text description of some of the findings, as well as a sentence describing potential impacts. This section appears in the Attestation Report and Full Report formats.
- Scope of Work: A more detailed description of the assets covered by the pentest. This includes constraints or assumptions that could impact a tester’s ability to fully test the in-scope assets. This usually matches the Statement of Work of an engagement.
- Summary of Findings: A bulleted list of the findings, and a summary of the details about them, organized by severity. Depending on the number of vulnerabilities discovered, the Low-risk and Informational findings may be left out.
- Summary of Recommendations: A numbered list of the remediation actions that the pentester recommends, organized by priority. These are usually high-level recommendations, with more detailed information in the Finding Report itself.
- When you’re done, change the report state to Final, and select Submit for Review.
- To save your work and continue to edit later, select Save.
- When you mark the report as Final, the pentest moves to Remediation. You can’t move the pentest back to the Live state.
All users who have access to the pentest can view and download the report.